
Civintec access control system/reader utilizes mobile credentials and 13.56MHz & 125KHz RFID smart card technologies to ensure convenient and reliable access control in corporate offices, government institutions
 Share
Share Download
Download
Civintec access control system/reader utilizes mobile credentials and 13.56MHz & 125KHz RFID smart card technologies to ensure convenient and reliable access control in corporate offices, government institutions, or large public venues. Role-based access control security system and solution provide a contactless access experience to help protect their government sector and keep the public safe.
The end-to-end security encryption technology focuses on protecting data as it is sent from access control reader to the third-party controller, and compatible with the most popular 13.56MHz RFID smart cards including MIFARE Classic®, MIFARE PIus® and DESFire®EV1/EV2/EV3 smart cards for high security.
Cidron access control reader supports Wiegand, Clock/Data, and RS485 interface to connect the third-party controller for security access control. It is compatible with MIFARE® SAM AV2/AV3 for EAL 5+ date store protection. Cidron access control reader supports OSDP Open Supervised Device Protocol (OSDPv2 secure channel) for bidirectional encrypted communication between reader and controller.
Civintec access control system/reader should support multiple layers of authentication to verify users’ identities. Government security systems could include (NFC/ BLE mobile, QR code, and PIN code) combined with RFID smart cards for access control. This layered approach reduces the risk of unauthorized access. The access control system must ensure that only authorized individuals can access sensitive areas and device in government institutions.
For Cidron reader, when user waves their access card or mobile credential over the reader, it sends a message to the third party controller, which then authenticates the credential to verify that the user is authorized to enter. If the credentials is valid, the controller sends a signal to the door lock instructing it to open.

For CT9 PRO, when user presents RFID, mobile credential or enter pin code on CT9 PRO, CT9 PRO sends access codes to server automatically via HTTP command, and server verifies the credential is valid and sends back command to CT9 PRO relay output for lock control, and open door.

Government institutions often have numerous departments and buildings. The access control system should be scalable to manage multiple access points across different area. It should also be flexible enough to accommodate changes in staff, departments, or security policies. Role-based access control security system can control who can access your site for different levels of personnel at different time periods. For example, the staffer can access corporate offices from 9:00 am to 17:00 pm during the day. The other worker can enter building from 9:00 am to 11:00 pm during the day. Manager can add and revoke access rights for different levels of staff from Cloud/PC in real time.
A comprehensive approach to security involves integrating access control systems with other security infrastructure, such as fire alarm systems, and intrusion detection. This creates a cohesive security environment where real-time monitoring and response capabilities are optimized. CT9 PRO access control system features relay I/O port that can be connected to the fire alarm system for immediate alarm notifications. Access control system must facilitate quick, safe evacuation. It should allow for immediate unlocking of doors or granting temporary access to emergency responders while maintaining overall security integrity.
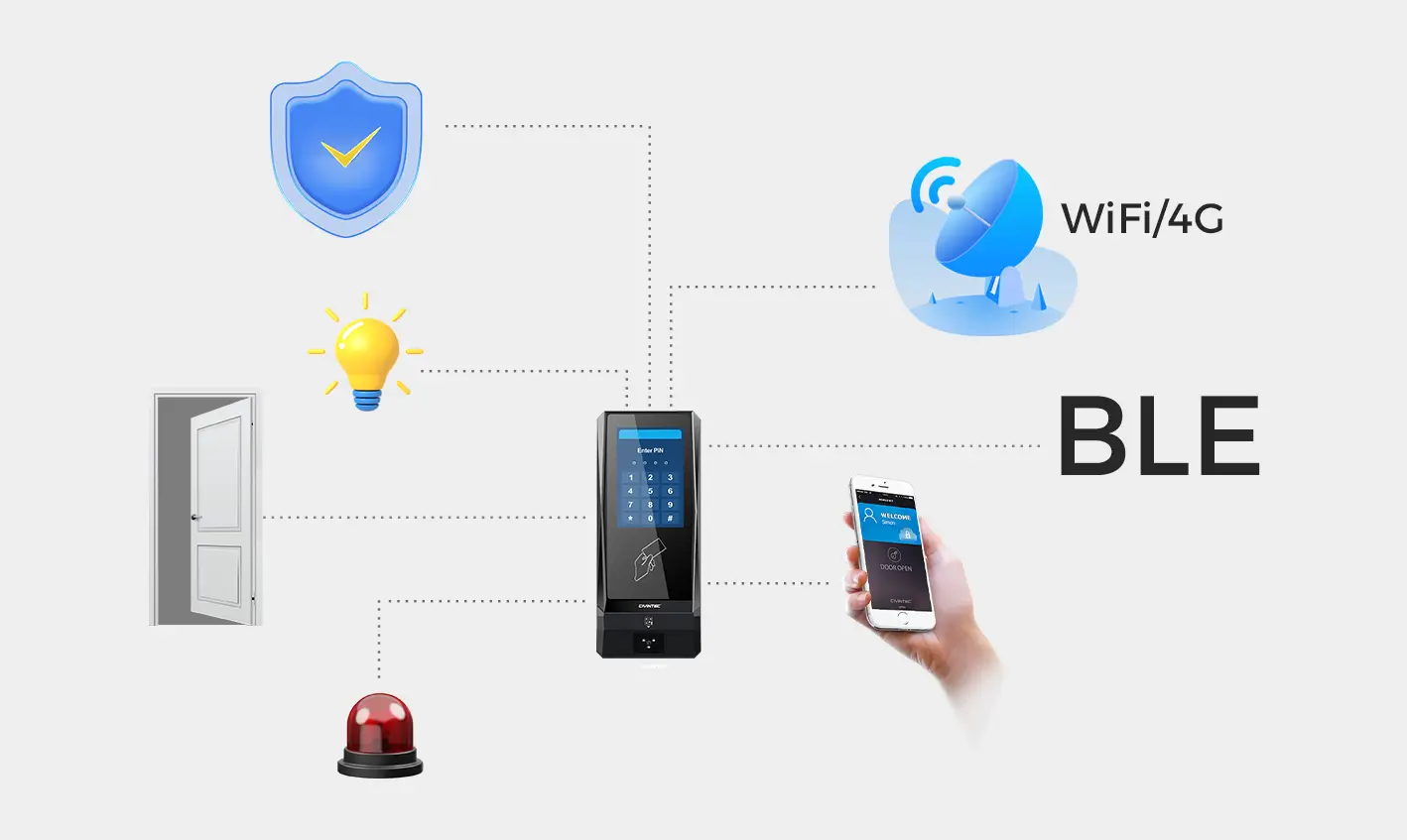
Every day, there are different levels of personal entering and leaving different areas in government agencies. CT9 PRO access control system should integrate with government databases or HR systems for seamless user management, including automatic provisioning and de-provisioning of access as staff join or leave the institution. The system controls who has access to what areas and when. It can manage user profiles, access permissions, and generate reports for employee time attendance management.
Government security system that allows security personnel to monitor real-time activity, review access logs, and receive alerts for any suspicious activity. The access control system can be hosted either on-premises or in the cloud. Cloud-based system CT9 PRO supports wire TCP/IP and wireless WAN like 4G, Wi-Fi, BLE internet. Real-time synchronization of events and logs to the Cloud/PC through HTTP/Https encrypted communication protocol. This technology provides remote management capabilities and easy scalability, while on-premises systems offer greater control for highly sensitive areas.

An overall and well-designed government security systems is essential for protecting government institution from unauthorized access and safeguarding sensitive areas and assets. By implementing a multi-layered security methods, integrating advanced technologies like mobile access, 13.56MHz & 125KHz RFID card, and real-time monitoring, fire alarm system, and ensuring regulatory compliance, government organizations can significantly reduce security risks and enhance the overall safety of their facilities.

